Tunneling ssh – option 1
See the previous post for an explanation of what we’re trying to accomplish.
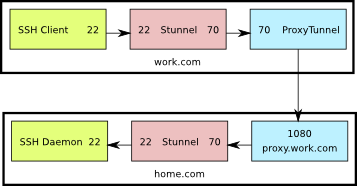
This is a diagram of what the setup looks like. The numbers shown are the TCP ports used by the various components.
Start by creating a certificate and key to be used by Stunnel (or reuse the web server certificate if you already have one).
Configure Stunnel on the server (/etc/stunnel/stunnel.conf) as follows:
cert = /etc/ssl/certs/home.com.crt key = /etc/ssl/private/home.com.key sslVersion = SSLv3 chroot = /var/lib/stunnel4/ setuid = stunnel4 setgid = stunnel4 ; PID is created inside chroot jail pid = /stunnel4.pid ; Service-level configuration [stunnel-ssh] accept = 70 connect = 22Also on the server, configure libwrap In
/etc/hosts.allow:
stunnel-ssh: ALLOn the client PC, this is the proxytunnel command line you'll need to use:
C:\>proxytunnel.exe -p proxy.work.com:1080 -d home.com:70 -a 70Configure the work.com stunnel:
sslVersion = SSLv3 ; Use it for client mode client = yes [stunnel-ssh] accept = 22 connect = 70
Restart stunnel on the server side, and open up port 70 on the firewall.
On the client side:
- Start proxytunnel using the command shown above.
- Start stunnel. If the stunnel.conf file is in the default location, no command line arguments are needed. If not, pass the config line as a command line argument to stunnel.
- Start your ssh client and connect to 127.0.0.1:22
Here’s what’s going on:
- The ssh client connects to port 22 on the localhost
- Stunnel is listening on port 22 on the localhost, so it receives that connection and sends it on to port 70 also on the localhost
- ProxyTunnel is listening on port 70, so it takes that connection from Stunnel and sends it to home.com:70 through proxy.work.com:1080
- Stunnel is listening on port 70 at home.com and when it receives the connection from Apache, it sends it to port 22 on home.com
- Finally, sshd is listening on home.com:22 so it receives the connection from Stunnel, allowing the user to log in
This is by no means optimal. Packets are encrypted twice: once by ssh and once by stunnel. In the end though, if you have no other option, this should work.
Wouldn’t you be able to cut out the stunnel at work.com by using ‘proxtunnel –encrypt’?
How does one create a certificate?
Eludias, I have the same question; I believe proxytunnel -e supports the same functionality as the stunnel setup above.
Here is how I created my certificate (originally for my apache server, but I reused)
openssl req $@ -new -x509 -days 365 -nodes -out /etc/apache2/apache.pem -keyout /etc/apache2/apache.pem
@assem
actually, I would like to retract my previous statement about proxytunnel and the -e option.
upon reading the man page again, I believe it means it would ask for encryption between the local proxy and our destination (but we don’t trust the local proxy!)
I guess there is no alternative setup for the given configuration w/proxytunnel ?